Are you a potential Cyber Crime Target

Rethinking your approach to Cyber crime is of paramount importance, it does not only effect safeguarding your online financial transactions and personal information. It effects everything that is contained on your phone – laptop and corporate network. In times of market volatility, the risk of cyber fraud increases as criminals exploit the movement of money between banks and financial institutions. To help you understand and protect yourself against cybercrime, Paul Somers (ex-IT Compliance & Governance implementor) explains some of the product areas our cybersecurity team focuses on.
Understanding Cybercrime
Cybercrime encompasses various activities such as phishing, business email compromise, and impersonation attacks, where criminals try to gain unauthorized access to sensitive information and systems. For most individuals, cybercrime involves traditional criminal activities targeting personal financial data and monetary theft. These criminals, whether individuals or organized groups, possess advanced skills and employ technology to carry out their theft.
How Cybercrime Operates
Cybercriminals employ different strategies depending on their objectives. They may cast a wide net with phishing scams, hoping to catch a large number of victims, or they may specifically target high-net-worth individuals. In the latter case, criminals invest considerable time and effort to identify valuable targets, create victim profiles using publicly and privately available information, and then execute asset theft from financial accounts.
While the methods of cybercrime may vary, the underlying steps often follow a similar pattern:
- The criminal sends an email to the victim, appearing to be from a trusted source, with a link or attachment. When the victim clicks on it, malware infects their computer.
- Using the installed malware, the criminal steals the victim’s login credentials or gains remote control of their computer, allowing them to log in as the victim.
- With access to the victim’s accounts, the criminal alters the victim’s profile at the financial institution and/or impersonates the victim to transfer money to criminal accounts at another institution.
Protecting Yourself from Cybercrime Fortunately, there are steps you can take to bolster your defences against cybercrime:
-
Safeguard your online access: Use unique user IDs, strong passwords, and enable two-factor authentication (2FA) for each website you visit. Implementing 2FA adds an extra layer of security by requiring a unique security code, generated and sent to your mobile device, in addition to your standard login credentials.
-
Secure your devices and keep them up to date: Use modern operating systems and keep them updated, along with your software and antivirus protection. Perform regular backups of your data to prevent loss and protect against ransomware attacks.
-
Be cautious with email links: Avoid accessing financial accounts or e-commerce sites through links provided in emails, as cybercriminals often impersonate trusted institutions. Instead, use bookmarks or saved links to access websites directly. Always verify the legitimacy of email requests for money transfers by contacting the person or institution through a trusted phone number.
-
Ensure Wi-Fi security: Change default Wi-Fi network names and passwords to enhance security. Be cautious when using public Wi-Fi networks, as they can be easily intercepted by attackers. Consider using secure paid hotspot providers when traveling.
-
Consider a dedicated device for online banking: Use a separate device exclusively for banking and financial transactions to reduce the risk of malware installation.
-
Understand your computing environment and seek help if needed: Assess your specific needs and consider additional security measures, such as intrusion prevention, firewalls, and ongoing system surveillance. For complex environments, consulting a professional firm for ongoing support and maintenance can be beneficial.
Conclusion
Taking proactive steps to protect yourself against cybercrime is crucial in today’s digital landscape. By adopting good system hygiene practices and making small changes to your online habits, you can significantly enhance your security. Zettabytes provides advanced security measures and additional tools like 2FA and transaction alerts to protect customers, and encourages regular monitoring of accounts for any suspicious activity. Call us to organise a customer security site inspection.
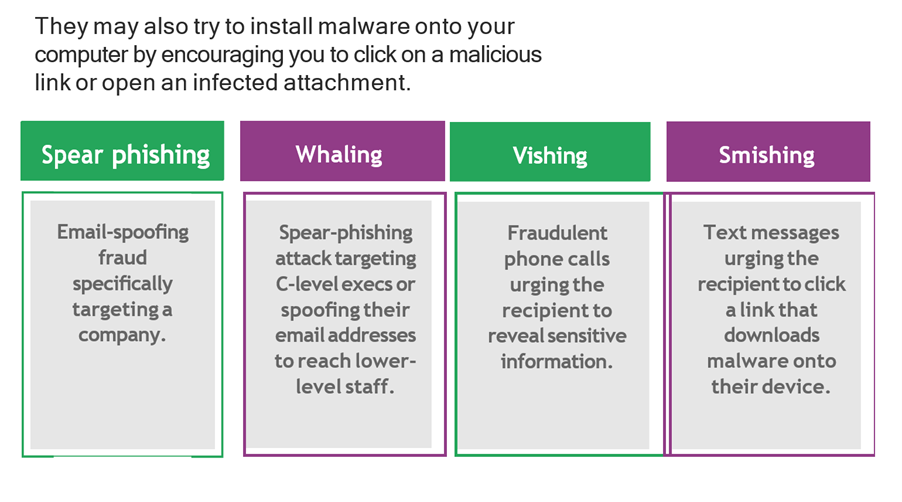
Reinforce staff awareness of phishing with this bundle, which comprises the bestselling Phishing Staff Awareness E-learning Course. Teach staff how phishing attacks work, the tactics employed by cyber criminals and what to do when you are targeted.
- Instil phishing knowledge in a fun way.
- Test your employees’ phishing knowledge.
- Encourage a culture of cyber security awareness in your organisation.
What’s included in the package?
Phishing Staff Awareness E-Learning enables us teach staff how phishing attacks work, the tactics employed by cyber criminals and what to do when you are targeted.
The course covers:
- What social engineering is.
- How to identify social engineering attacks.
- The consequences of a phishing attack.
- How easy it is to fall victim.
- How phishing attacks are orchestrated.
- How to identify a phishing scam; and
- Ground rules for avoiding phishing scams.