Firewall as a Service
Stop viruses, spyware, worms, Trojans, key loggers, and more before they enter your network, with all-in-one, comprehensive network protection. SonicWall provides you with the same level of network security that NASA demands and protects your network from a wide range of emerging threats.

This is why we use SonicWall
The growing use of cloud computing, mobile solutions, bring your own device (BYOD) policies and the rise of shadow IT have added new levels of risk, complexity and the cost to securing an organization’s data and intellectual property.
Organizations of every size must now combat a wide range of increasingly sophisticated threats, including advanced persistent threats (APTs), cybercriminal activity, spam and malware. At the same time, many organizations are also grappling with tighter budgets and don’t have the resources to easily address their growing security challenges.
Zettabytes can take away the risk with our affordable centrally managed firewall service, using SonicWALL which helps your compliance and security objectives by managing and monitoring your firewall appliances.
Our proactive services provide, 24/7 administration and support for multiple network security functions including:
- IPS/IDS
- Firewall
- Antivirus
- Anti-spyware
- Application control
- Content filtering
- Wireless LAN
- VPN tunnels
- Multi Wan support
Zettabytes offers our Managed Firewall Services as an annual service subscription in which zettabytes security personnel connect to a firewall and manage it on your behalf. This offer includes access to all the zettabytes portal where you can see the status of devices, view a security dashboard and create tickets to request configuration changes.
Keeping you safe
Zettabytes also monitors the firewall 24 hours a day looking for signs of attack or intrusion. While all security incidents are validated, only critical incidents are escalated to the end user.
Licensed model information
- Management and 24/7 security monitoring services for the Sonic wall firewall
- Performance and availability management
Entry points into your network may now include employees’ laptops, desktops, and smartphones. Secure your network and data against sophisticated, modern-day threats with comprehensive protection that includes intrusion prevention, gateway anti-virus, anti- spyware, content/url filtering, enforced client anti-virus, and anti-spam services.
The amount of traffic being scanned by your firewall, as well as the increasing amount of threats and malware attacking it, is quickly becoming more than many firewalls can handle. SonicWall is designed to protect organizations of every size without slowing down your network — providing you with fast, reliable performance.
Your network performance can be bogged down by spam, unauthorized web activity and social networking traffic that have nothing to do with getting work done. Ensure your business-critical applications have the bandwidth they need with content and application control tools.
Your employees need access to email, files and applications wherever they are. Now you can allow mobile users to access your network with secure VPN remote access for Windows, Apple iOS, Android, Mac OS X and Kindle Fire devices and be assured that it is safe,secure, and free from threats.
Combine the features of traditional firewalls, gateway anti-malware products, intrusion prevention systems and content filtering software in a single solution. All of these security technologies are installed, configured, deployed, and managed as one unit. Detailed event data is available through one reporting system so it is easier to identify threats early and take appropriate measures BEFORE your network has been compromised.
- Block viruses, Trojans, worms, rootkits and polymorphic “zero-day” malware at the gateway, before they reach your network.
- Prevent “drive-by downloads” from infected websites.
- Mitigate denial-of-service and flooding attacks.
- Detect protocol anomalies and buffer overflow attacks.
- Stop network traffic from geographical regions and IP addresses associated with cybercriminals.
- Block outbound cybercriminals botnet “command and control” traffic from stealing your customer lists, engineering designs, trade secrets, and other confidential information.
- Control access to websites containing unproductive and inappropriate content.
- Ensure high-priority applications (CRM, order processing) receive more bandwidth than less urgent applications (chat, video streaming
- Outsource your network security to an experienced security provider.
- Firewall expertly configured by SonicWall-certified engineers.
- Turn-key solution delivered to your doorstep.
- Proactive monitoring and alerting
- Updating of firmware, software, and security updates
- Automated weekly network and security reports
- Report analysis by SonicWall-certified engineers
- Weekly off-site SonicWall configuration backup
- Upgrade appliance as future business and technology changes dictate
- Device upgrades and patch management
- Real time security and health monitoring
- Expert response to threats and health issues
- On demand security and compliance reporting
- Management and monitoring will be delivered via a Sonic wall GMS console that is hosted by us providing:
- Real time security monitoring
- Device health monitoring
- Expert response to threats
- Annual fixed costs
Cloud Edge Security
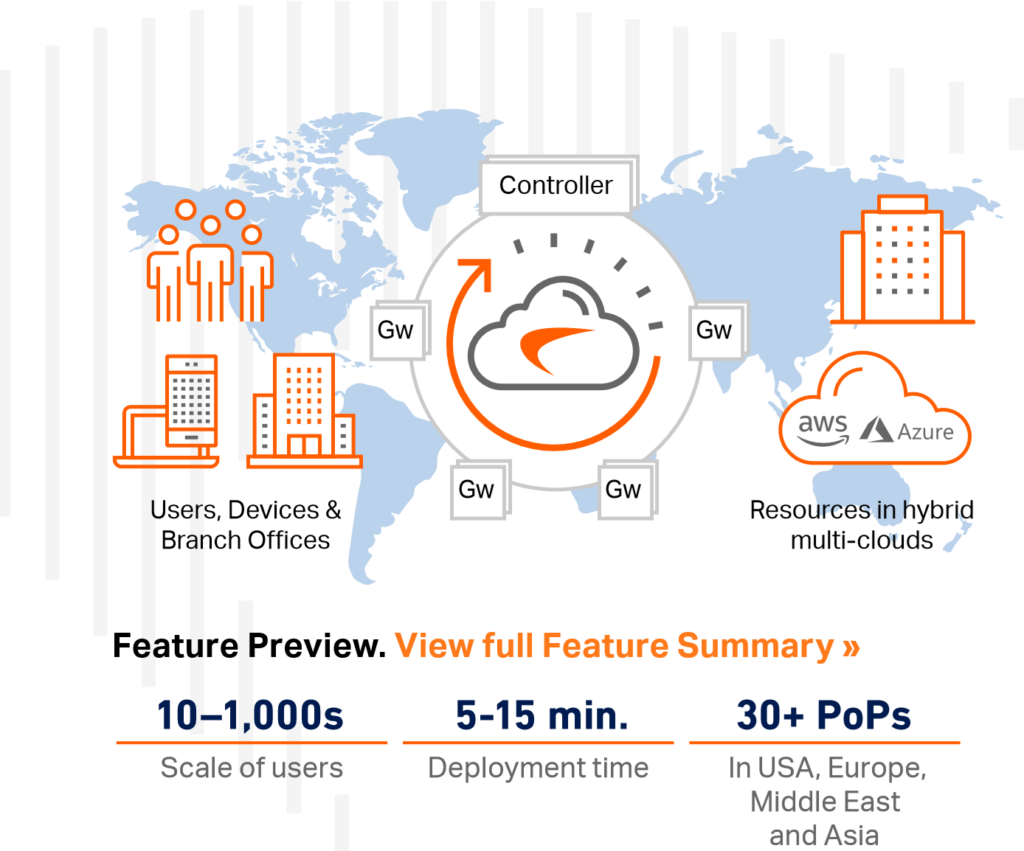 Typically the SonicWall Firewall is used for clients over 10 users, whereas due to the way that we have set it up in Zettabytes, we provide ‘SonicWall Firewall as a Service’ using Sonicwall cloud edge secure assets which we provide to our clients for site to site and hybrid cloud connectivity to AWS, Azure, Google Cloud and more. This combines Zero-Trust, Least- Privileged security and software-defined micro-segmentation to permit users and devices to access only what’s necessary and nothing more similar to a concept of a “need to know basis”.
Typically the SonicWall Firewall is used for clients over 10 users, whereas due to the way that we have set it up in Zettabytes, we provide ‘SonicWall Firewall as a Service’ using Sonicwall cloud edge secure assets which we provide to our clients for site to site and hybrid cloud connectivity to AWS, Azure, Google Cloud and more. This combines Zero-Trust, Least- Privileged security and software-defined micro-segmentation to permit users and devices to access only what’s necessary and nothing more similar to a concept of a “need to know basis”.
Now, organizations can offer remote work flexibility, preserve operational flexibility and at the same time protect high value assets from costly secure breaches.
HIGHLIGHTS
- Zero-Trust with software-defined micro-segmentation policies effectively prevent breach from spreading.
- Supports Single Sign-On and Multi-Factor Authentication using LDAP, Okta, Google, and Azure Identity Provider services.
- Network Traffic Control (NTC) is a stateful firewall[1]as-a-service (FwaaS) that provides policy-based protection by defining who can access what resource and from where.
- Device Posture Check (DPC) grants network access only to authenticated and compliant devices.
- Client apps are available for macOS, Win10, Android and iOS operating systems.
- Supports client-less Remote Desktop access using RDP, VNC, SSH and HTTP/ HTTPS for web access with any public devices.
- Provides better user experience with the fast and modern WireGuard secure tunnels.
- Always-on VPN emulates in-office experience and maintains strong security posture in public hotspots.
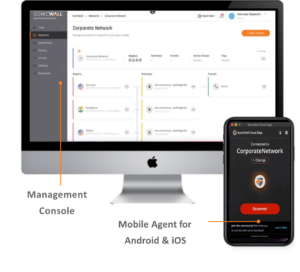
- Supports an easy drag-drop policy configuration interface to save time, and a dashboard to simplify compliance audits.
- Network monitoring provides a comprehensive overview of traffic pattern, and security postures of users, groups and servers.
Zero-Trust Network Access applies explicit trust approach that limits exposure to sensitive areas of the network to safeguard business assets
Traditional VPN solutions are not built for the cloud era. Some of the inherent problems include implicit trust allowing threats to move laterally inside the network, often long-lead deployment time, and increased cloud latency due to traffic hair-pinning, which impacts user quality of experience.
Gartner predicts that by 2023, 60% of enterprises will phase out most of their remote access virtual private networks (VPNs) in favor of ZTNA
SonicWall Cloud Edge Secure Access is built around Software-Defined Perimeter (SDP), an advanced and cloud-native architecture, to deliver rapid deployment and self-service onboarding.
- Faster deployment – An IT manager can sign up, create a gateway, and configure granular policies based on network and user context — all in less than 15 minutes.
- Faster user onboarding – An end user can choose whether to connect via their mobile device or desktop client app, or bypass client installation altogether when using a public computer, provided a browser is available. With the self-service deployment model, onboarding can be completed in 5 minutes.
- SDP is also secure by design because it decouples the controller, which authenticates users and devices, from the gateways that act as trust brokers. By distributing the gateways close to the end-user locations, Cloud Edge Secure Access can scale rapidly as needed, maintain high-performance and deliver the best cloud experience possible.
This separation of functions also enables Cloud Edge Secure Access to stop common cyberthreats, such as DDoS, public Wi-Fi hijacking, SYN flood and Slowloris.
Software-Defined Micro-Perimeter Security That Follows Users
Today’s employees want the flexibility to work from anywhere — and organizations want to take advantage of the cost savings and operational efficiencies offered by the cloud. In this new inverted reality, where everything is outside of centralized locations and beyond physical firewall
protection, there is a need to complement the current on-premises service delivery model with an agile follow- the-user security model.
With the SonicWall Cloud Edge Secure Access, the perimeter is software-defined, meaning each micro-perimeter segment encapsulates a particular type of traffic flow, defined by access policies. The segment starts with the user and extends to specific networks or services or assets anywhere
in the cloud — a much more versatile approach.
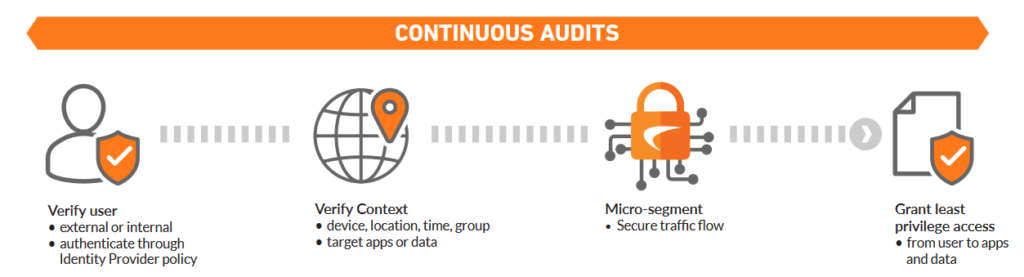
Zero-Trust Network Access
Trust Nothing and Verify Everything
- Zero-Trust policies allow you to have a proper set of contexts to securely access your host network Zettabytes with multiple resources using the supports of:
- Federated Single Sign-On and Multi-Factor Authentication – This combination provides users a single portal for authenticating into a hybrid IT environment, creating a consistent and seamless experience.
- Integration with our leading cloud-based identity management provider
- Context-driven access with Device Posture Check (DPC) – grants network access only to compliant and authorized devices that pass OS integrity and malware-free environment verifications to ensure no
malware slips into the infrastructure. - Software-defined micro-segmentation – Network Traffic Control (NTC) precisely segments all incoming traffic to prevent malware or unauthorized users from compromising network resources and sensitive data.
- Least-Privilege Access Control – Organizations can control user interactions with resources based on relevant attributes, including user and group identity and the sensitivity of the data being accessed.
Work-from-Anywhere Securely From Trusted Areas to Public Hotspots
- Automatic Wi-Fi security – Cloud Edge Secure Access for Windows and mac OS proactively monitors the environment, and automatically activate a secure access connection in public hotspots. This extra layer of protection stops Wi- Fi intercepts, which are increasingly common and can result in data thefts and compliance violation.
- Kill switch – When a secure access connection is interrupted, the device’s internet connection is instantly halted — disrupting potential cyber breaches and preventing any data from leaving the device.
- Trusted Wi-Fi networks – When an SSID is specified as “trusted,” the automatic Wi-Fi security feature will not activate.
- Always-on VPN/applications – This convenient feature automatically reconnects to an application or set of applications without requiring users to login or authenticate again.
Site-to-Site Interconnectivity or Network-as-a-Service (NaaS)
Our Cloud Edge Secure Access offers the choice of site-to-site connectivity service or Network-as-a-Service (NaaS), which we can use to quickly onboard your offices or personnel in geographically dispersed locations. This allows us to quickly and securely connect mobile kiosks, retail stores and sales points to cloud-hosted resources without needing to rely on costly MPLS.
- Site-to-site or site-to-cloud interconnect service – The solution easily connects to popular cloud environments, including AWS, Azure and Google Cloud — or can be used to create a secure communication link between networks located at different sites.
- Multi-regional deployment – Administrators can deploy dedicated Cloud Edge gateways in different locations to deliver optimal speed and performance to international branches and employees.
- High-performance global backbone – SonicWall Cloud Edge service is available globally. The infrastructure offers minimal latency by distributing gateways close to the customer locations and load-balancing traffic across servers.
- State-of-the-Art WireGuard secure tunnel – An IT manager can leverage any branch router or firewall with IPsec to connect to the nearest Cloud Edge gateway.SonicWall recommends the WireGuard tunnel, which
can deliver much faster performance. This deployment requires a branch Linux server to run the WireGuard tunnel service to the nearest gateway.




