
The Zero Trust Platform
The Zero Trust security solution that offers a unified approach to protecting users, devices, and networks against the exploitation of zero day vulnerabilities.
What is Ringfencing™?
Ringfencing™ controls what applications are able to do once they are running. By limiting what software can do, ThreatLocker® can reduce the likelihood of an exploit being successful or an attacker weaponizing legitimate tools such as PowerShell.
Ringfencing™ allows you to control how applications can interact with other applications. For example, while both Microsoft Word and PowerShell may be permitted, Ringfencing™ will stop Microsoft Word from being able to call PowerShell, thus preventing an attempted exploit of a vulnerability such as the Follina vulnerability from being successful.
Why Ringfencing™?
Under normal operations, all applications permitted on an endpoint or server can access all data that the operating user can access. This means if the application is compromised, the attacker can use the application to steal or encrypt files.
Attackers can also use file-less malware which runs in the computer’s memory, to evade detection by antivirus or EDR that are focused on detecting changes to files or registry keys. These attacks, often called living off the land attacks, leverage native tools and trusted applications to carry out malicious instructions in the background without ever touching the file system.
How Does Ringfencing™ Work?
When you first deploy Ringfencing™, your device will be aligned with the default ThreatLocker® policies. These policies are then automatically applied to a list of known applications such as Microsoft Office, PowerShell, or Zoom. The aim of the default policies is to provide a baseline level of protection for all endpoints. Each of these policies can easily be manipulated to fit any environment at any time. Our dedicated Cyber Hero Team is always on hand to support any requests, 24/7/365.
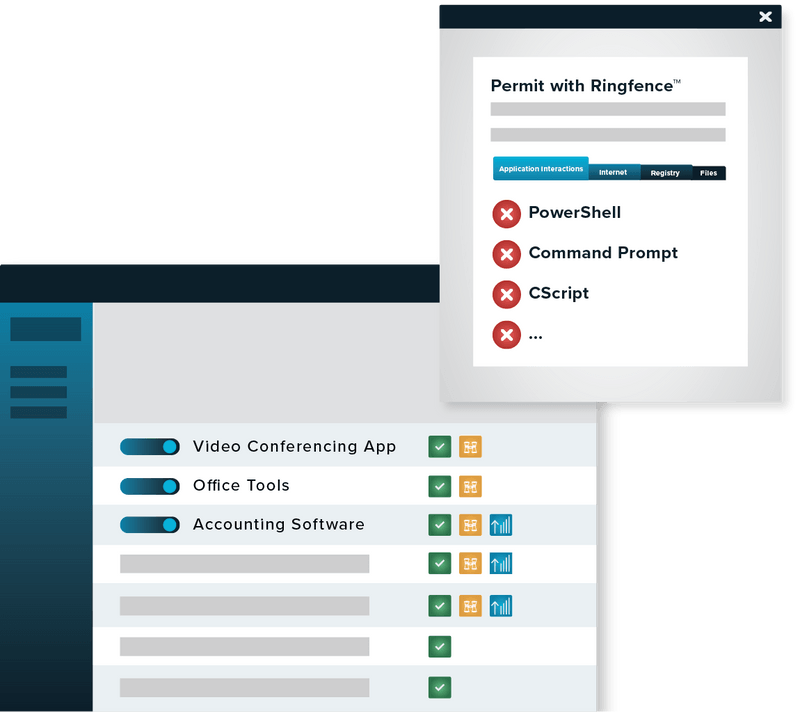
Preventing Software Exploitation
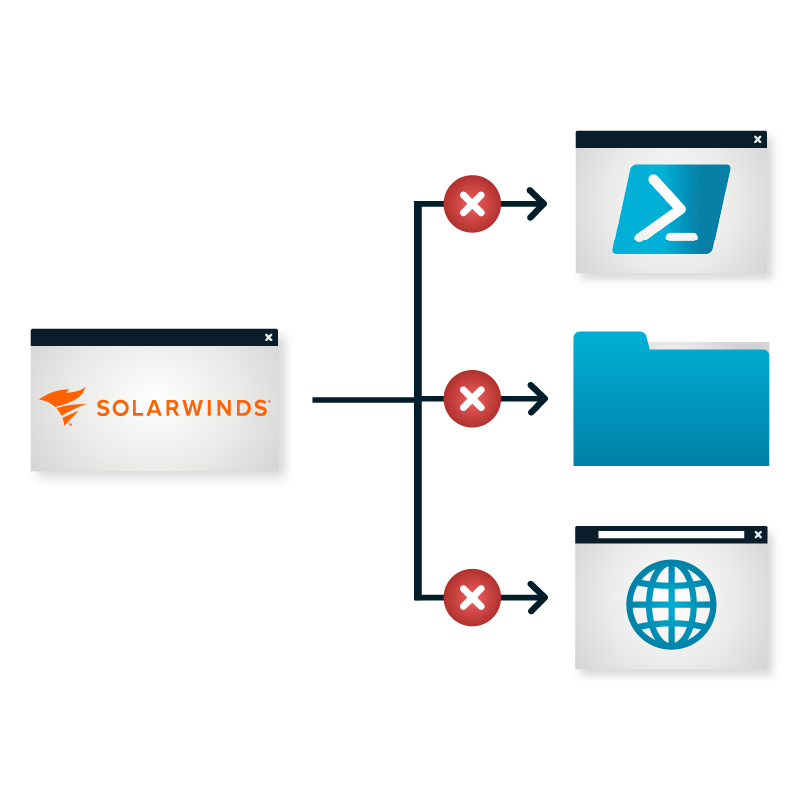
Ringfencing™ was able to foil a number of attacks that were not stopped by traditional EDR. The 2020 SolarWinds Orion attack was foiled by Ringfencing™. See how Ringfencing™ allows you to remove file access permissions for applications that do not need access and even remove network or registry permissions.
Protect your data from malicious behaviour
- Stop fileless malware and limit damage from application exploits
- Define how applications integrate with other applications
- Stop applications from interacting with other applications, network resources, registry keys, files, and more
- Stop applications from interacting with built-in tools such as PowerShell, Command Prompt and RunDLL
- Stop built-in tools from accessing your file share
What is Allow listing?
Application Allowlisting formally known as, “Application Whitelisting”, denies all applications from running except those that are explicitly allowed. This means untrusted software, including ransomware and other malware, will be denied by default.
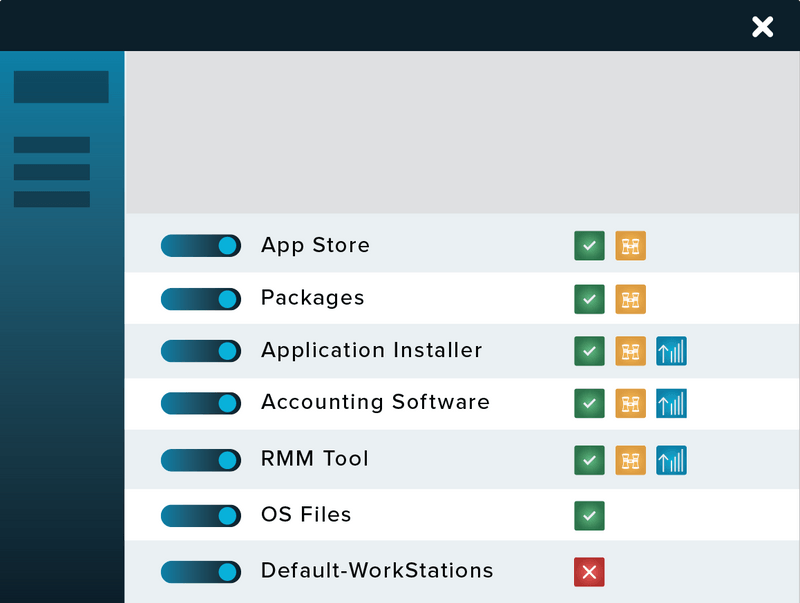
How Does Application Allowlisting Work?

When the agent is first installed, it operates in Learning Mode. During this period all applications and their dependencies that are found or running on the computer are catalogued and policies are created to permit them. After the learning period, the IT administrator can review the list of applications, remove those that are not required, and secure the computer. Once the computer is secured, any application, script, or library that tries to execute that is not trusted will be denied. The user can request new software from the IT administrator, and it can be approved in 60 seconds.
Why Allowlisting?
Application Allowlisting has long been considered the gold standard in protecting businesses from known and unknown malware. Unlike antivirus or traditional EDR, Application Allowlisting puts you in control of what software, scripts, executables, and libraries can run on your endpoints and servers. This approach stops not only malicious software but also stops other unpermitted applications from running. This process greatly minimizes cyber threats and other rogue applications running on your network.
Digital Trail with Unified Audit
The Unified Audit provides a central log of all storage access by users on the network and those working remotely, down to the exact files that were copied and the device’s serial number.
What is Storage Control

Storage Control provides policy-driven control over storage devices, whether the storage device is a local folder, a network share, or external storage such as a USB drive. ThreatLocker Storage Control allows granular policies to be set, which could be as simple as blocking USB drives, or as detailed as blocking access to your backup share, except when accessed by your backup application.
How does Storage Control Work?
When a storage device is blocked, the user is presented with a pop-up where they can request access to the storage device. The administrator can then choose to permit the storage device in as little as 60 seconds.
Eliminate the Risk and Guesswork
In addition to Allowlisting, ThreatLocker Testing Environment is a powerful tool that allows for risk-assessed approvals that eliminate the guesswork. The Testing Environment enables administrators to quickly verify an application, providing the critical and timely information needed to make the best decision for their organization.

Network Access Control: Cloud-managed endpoint and server firewall with dynamic ACLs to lockdown your endpoints and block unwanted network traffic.
Network Access Control allows for total control of inbound traffic to your protected devices. Using custom-built policies, you can allow granular access based on IP address or even specific keywords. Unlike a VPN that needs to connect through a central point, the ThreatLocker NAC is a simple connection between server and client. ThreatLocker NAC is built in a way that creates a seamless experience, enabling users to work as normal while eliminating the need for a solution, such as a VPN.







